用户可能有多种身份,创建实体时绑定一个基本策略,然后创建多个别名,每个别名绑定不同的认证方法。认证方法可以绑定单独的策略。当用户使用不同的方法入口登录,具有的权限不一样,可以访问不通的秘密。这有点像切换角色。
Why create entities?,官方解释把用户换成应用的概念,那么应用可以有不同的认证方式,例如用户名密码,OIDC,LDAP等。无论是哪种方式登录都应该视作同一个客户端,这样Hashicorp就不会重复计数,因为收费版本可能是按照客户端数量收费的。
Vault 1.15.0提供了14中认证方法。
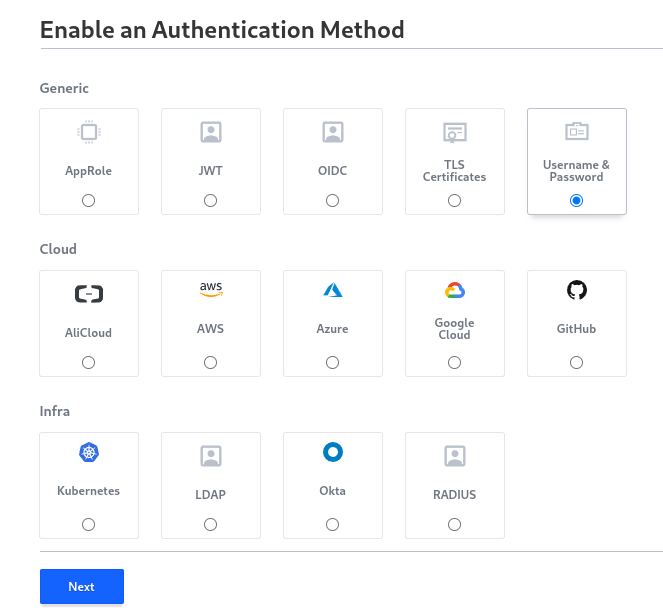 Vault Authentication Method
Vault Authentication Method
- AppRole
- JWT
- OIDC
- TLS Certificates
- Username & Password
- AliCloud
- AWS
- Azure
- Google Cloud
- GitHub
- Kubernetes
- LDAP
- Okta
- RADIUS
1
2
3
4
5
6
7
8
9
10
11
|
curl --request POST \
--data '{"password": "wffgerqa"}' \
$VAULT_ADDR/v1/auth/userpass-qa/login/wffgerqa \
| jq -r ".auth.client_token" > qa_token.txt
curl --request POST \
--data '{"password": "wffgertest"}' \
$VAULT_ADDR/v1/auth/userpass-test/login/wffgertest \
| jq -r ".auth.client_token" > test_token.txt
|
1
2
3
4
5
6
7
|
tee payload_test.json <<EOF
{
"data": {
"designer": "ydx"
}
}
EOF
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
curl --header "X-Vault-Token: $(cat test_token.txt)" \
--request GET \
$VAULT_ADDR/v1/secret/data/test
curl --header "X-Vault-Token: $(cat qa_token.txt)" \
--request GET \
$VAULT_ADDR/v1/secret/data/test
curl --header "X-Vault-Token: $(cat test_token.txt)" \
--silent --output /dev/null --write-out "%{http_code}\n" \
--request POST \
--data @payload_test.json \
$VAULT_ADDR/v1/secret/data/test
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
[wffger@ydx vault]$ cat test_token.txt
hvs.CAESIM4UBwF-QeQSZn4N_zNloj06RTzuFOsCcMEseq2bAmVTGh4KHGh2cy5CY3FDVWxaeXphVXludWNERndiOTlKd2w
[wffger@ydx vault]$ curl --header "X-Vault-Token: $(cat qa_token.txt)" \
--request GET \
$VAULT_ADDR/v1/secret/data/test
{"errors":["permission denied"]}
[wffger@ydx vault]$
curl --header "X-Vault-Token: $(cat test_token.txt)" \
--request GET \
$VAULT_ADDR/v1/secret/data/test
{"request_id":"ebd2ff41-dcdf-1858-82bd-a8f522a90fe2","lease_id":"","renewable":false,"lease_duration":0,"data":{"data":{"product":"mate70","release_date":"20231012"},"metadata":{"created_time":"2023-10-09T10:31:34.664826713Z","custom_metadata":null,"deletion_time":"","destroyed":false,"version":1}},"wrap_info":null,"warnings":null,"auth":null}
[wffger@ydx vault]$ curl --header "X-Vault-Token: $(cat test_token.txt)" --silent --output /dev/null --write-out "%{http_code}\n" --request POST --data @payload_test.json $VAULT_ADDR/v1/secret/data/test
200
[wffger@ydx vault]$ curl --header "X-Vault-Token: $(cat test_token.txt)" --request GET $VAULT_ADDR/v1/secret/data/test
{"request_id":"74172cfc-7e54-39cf-264f-c6808e750fb5","lease_id":"","renewable":false,"lease_duration":0,"data":{"data":{"designer":"ydx"},"metadata":{"created_time":"2023-10-09T10:44:31.249698334Z","custom_metadata":null,"deletion_time":"","destroyed":false,"version":3}},"wrap_info":null,"warnings":null,"auth":null}
》
|
